How to: set up mail encryption | GDPR Compliance for Recruiters
With the deadline for GDPR compliance now passed, businesses are looking for ways to refine their data security. But where do you start? One of the simplest steps you can take to demonstrate GDPR readiness is to add encryption to your mailing system.
Why encrypt?
The popular image of encryption is of something used only by hackers and criminals to hide their activities online. So why would you need to encrypt your mail?
In reality, encryption is one of the most reliable tools for safeguarding the way you share data and communicate. As GDPR introduces much tougher fines for data breaches, these considerations are no longer an afterthought for your business. Nor are they something you can think about, then decide to put off until a later date.
As we have previously explained, encryption will be considered best practice under GDPR as soon as regulations come into force this year. But do not be surprised if secure mail eventually becomes the expected standard for business communications on a daily basis. This cultural change could happen sooner than you think.
The final reason is perhaps the most compelling for recruiters on a GDPR compliance drive: because it looks good. Mail encryption shows clients and authorities that you take data security obligations seriously. You don’t have to encrypt every last note that you send out. But it is good to know you have a secure option in place for important data transfers when you need it.
Encryption: what is it?
So, encryption works. But exactly how does it work?
Think of it this way. You want to receive a secret message through the mail from a friend. You have an empty briefcase and a padlock to secure the message. If you don’t attach the padlock, then your message will be at risk of being stolen. But, if you attach the padlock to the briefcase, your friend will be unable to put the message inside.
To solve this puzzle, you send the empty briefcase, with the open padlock inside. The open padlock is your public key, which you can share freely. Your friend, on receiving the briefcase, places the important documents inside the case, and fastens it shut with the padlock (public key). With the padlock now closed, it can only be opened with the paired key. This is your private key – and only you have access to this. Once encrypted, even your contact cannot un-encrypt the original message again: even though they know both your public key, and the contents of the original message they sent you.
When the case is delivered, you unlock the padlock (the encryption) with the paired key (your private key). You have now received the important documents, and at no point in their delivery were they left unsecured or at risk of theft. That is encryption.
Step-by-step: Encrypting your email
Thankfully, once you have encryption set up, it is very easy to use. Even the set-up can be satisfyingly simple. For the purposes of this guide, we will use Mozilla Thunderbird. Don’t worry if you use a different mail client: it’s open source (meaning it’s free), and you can run it alongside your existing mail client. In fact, it may be useful to have a separate program for your encrypted mails.
1. First, download and install Mozilla Thunderbird.
2. Next, get the Enigmail add-on. Right-click the link and save it to your desktop. Left-clicking will install the add-on to your web browser, which we do not want.
3. The last tool you need is the Pretty Good Privacy (PGP) app, GnuPG. PGP has been described as “the closest you’re likely to get to military-grade encryption” as a private business. It can withstand brute force and maths-based attacks on your data. Windows users can download GPG4Win here.
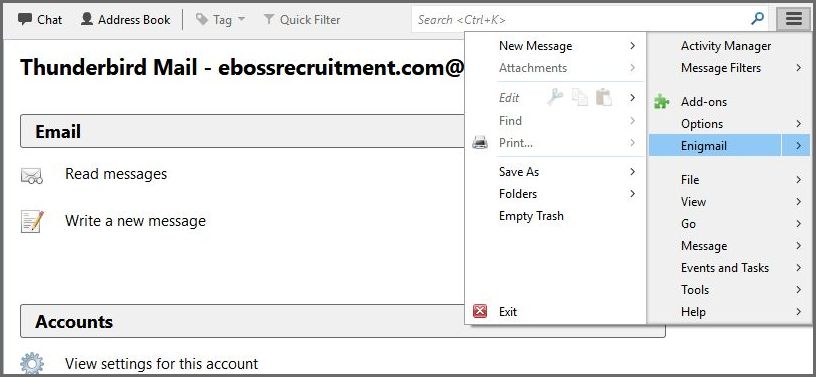
4. Open Thunderbird and, from the Options menu (three horizontal lines in the top right), choose Add-Ons, click the Tool icon, and select Install add-on from file. Open and install Enigmail. Restart the Thunderbird client.
5. Head back to the Thunderbird options menu: you should find a new ‘Enigmail’ option. Click that, and choose the Set-up Wizard.
6. Choose Standard Configuration, input your email account data, and choose a secure passphrase.
7. Wait for GnuPG to create your public and private keys. Once completed, you will be given the option to Create Revocation Certificate. This will be useful if your account is ever compromised and you need to change your passphrase settings. Generate the certificate, and save it to a USB thumbdrive. Keep this safe, and disconnect it from all online devices. Congratulations: you have set up your email encryption.
What’s different?
You can now send encrypted emails. But what does that actually mean?
When you set up your account you generated a passphrase. This passphrase created a public and a private key. With these keys, you can send and receive mail securely with trusted contacts.
You can attach your public key to any email and, from this, the recipient will be able to encrypt a message that only you can read.
Your private key (passphrase) is then used to unencrypt the message within your inbox. You must never share your private key with anybody.
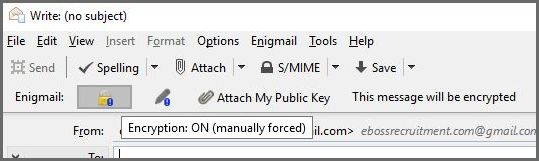
Sending Mail
The good news is that all of this can be achieved with just three buttons in the Thunderbird client. When you now compose a mail, you will see three new options:
eBoss and Encryption: Security for recruiters
When it comes to sharing, sending or receiving business data, eBoss will occasionally request a secure connection after GDPR regulations come into force. This is as much to ensure the integrity of your own data – and that of your data subjects – as it is to protect our own resources. For this reason, it might be appropriate to set up mail encryption now: so that you are not burdened with an unexpected workload at a crucial moment in the future.